- Overview
- Key Features
- Application and Software
- Network
- Device and Infrastructure Server
- Data Protection
- Detective Control
- IAM – Authentication and Access
- Compliance
- Government Risk and Compliance (GRC)
- Security Operations and Incident Response (IR)
- Vulnerability Management
- Infrastructure Security
- Security Certifications and Accreditation
Technical Brief
Cloud Security
Highest levels of security controls for EDA workloads
Overview
Overview
Cadence OnCloud Managed Service platform has multi-layered security protection. It follows defense in-depth principles for the protection of systems and data. Cadence uses industry security frameworks, standards, and processes to manage its security and risks.
Key Features
Application and Software
Cadence software development teams follow a shift-left security practice within the software development lifecycle (SDLC) early and often as part of SecDevOps. Continuous security assessments are applied during development operations by integrated security tools at the source code repository, build, and artifact level. Scheduled and ad-hoc builds integrate static application security testing (SAST) to highlight areas in need of secure code review for sanitization, input validation, encryption standards, and other security flaws. Open-source software (OSS) security is enforced through vetted components within a closed build environment. Once the artifacts for software distribution are assembled, they are
scanned with software composition analysis (SCA) tools to complete supply chain assurance. Released products undergo dynamic application security testing (DAST) and manual penetration by internal and external vendors to expose misuse cases and identify weaknesses within the software. Cadence software deployed to hybrid cloud environments is protected with real-time application security protection (RASP), distributed denial of service (DDoS), and web application firewal (WAF) controls.
Network
The Cadence OnCloud Managed Service hybrid environment implements hardened security template designs and standards to ensure consistently applied security settings and controls for software deployment in the cloud. Secure cloud infrastructure is implemented with state-of-the-art edge protections for stateful inspection, global availability, redundancy, monitoring, and the separation and protection of customer data in this multi-tenancy environment.
Device and Infrastructure Server
All endpoints support endpoint detection and response (EDR) to identify malicious activities, communications, and standard signature-based threats. Endpoints are protected behind serverless APIs and provide user access to custom tool environments. Workloads are processed on dedicated instances to segregate customer data.
Data Protection
Strict user data separation and access controls are enforced throughout the shared tenancy. Data is encrypted at rest and in transit. Data at rest encryption with key management is enabled.
Detective Control
API-level audit logs, configuration change management, monitoring logs and alarms, automated threat detection, and integration with SIEM are in place
IAM – Authentication and Access
Single sign-on (SSO), multifactor authentication (MFA), and role-based access are all configured for the Cadence Cloud Platform.
Compliance
Compliance and governance and cloud security posture management (CSPM) are in place
Government Risk and Compliance (GRC)
Security Operations and Incident Response (IR)
Continuous threat monitoring and behavior analytics ensure cloud security baselines are enforced and maintained. SOC teams actively manage and respond to security incidences and behavioral
abnormalities. Additional responses include automated incident response actions, temper protection and tabletop exercise.
Vulnerability Management
Endpoints undergo monthly patching and scheduled vulnerability scans. The cloud infrastructure and serverless components are monitored for upgrade requirements. The component inventory is continuously monitored for new exploits and vulnerabilities.
Infrastructure Security
Infrastructure security upgrades include vulnerability assessment, automation and patch management, certificate management, DDoS attack protection, web application firewall, geographic restriction, stateful inspection firewall, and network access control lists (ACLs)
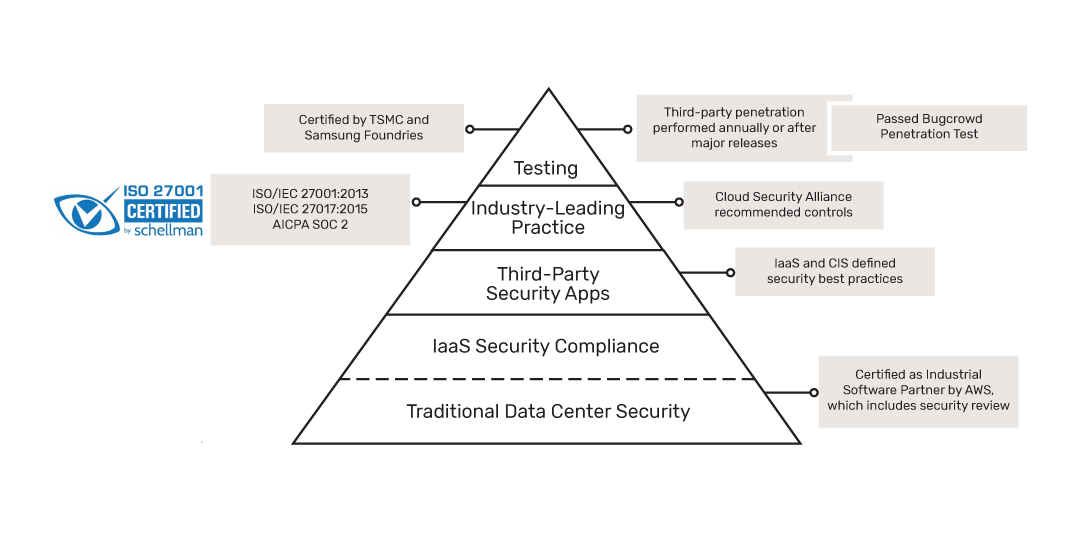
Security Certifications and Accreditation
Cadence developed the OnCloud platform in compliance with the ISO/IEC 27001, ISO/IEC 27017, and SOC 2 standards to address regulatory compliance and contractual obligations, and to demonstrate consistent security practices.
Cadence is working to get an independent attestation of its Information Security and Privacy practices for the OnCloud in-scope software applications and systems.
ISO/IEC 27001 and ISO/IEC 27017 are part of a family of Information Security Management System (ISMS) standards published by the International Organization for Standardization (ISO).
SOC 2 is a compliance standard for service organizations in safeguarding customer data, developed by American Institute of CPAs (AICPA).